I recently participated in a CTF hosted at BSides 2021 and completed a challenge I that I found pretty interesting, so I'm going to share it here. It's topic is malware reverse engineering. In this challenge we were given an encrypted and obfuscated rat payload and asked to find the IP address of the C2 server it beaconed to.
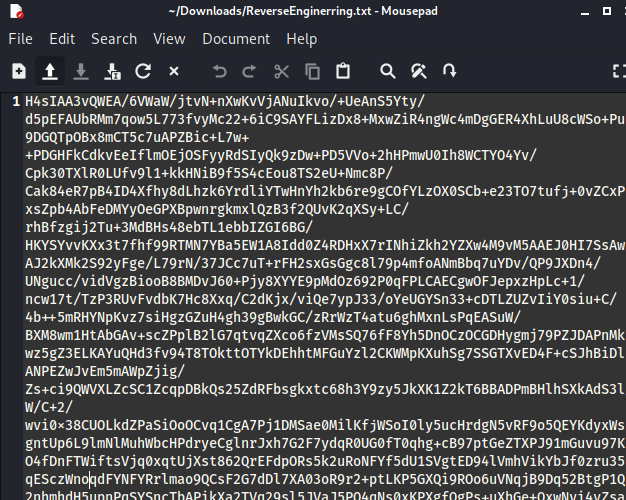
Just from looking at it, I can tell that it's base 64 encoded. When we decode this, we are given more jibberish.

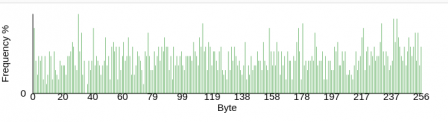
From here, I needed to decide whether it was encrypted, obfuscated, or just encoded. I ran it through a frequency analyzer and it output a relatively uniform distribution. This crosses out encoding and obfuscating, so it's safe to assume it's encrypted.
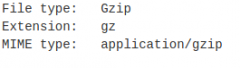
I then ran it through a file detector, and it showed confidence that the data was a gzipped.
So, I decompressed the data and finally, we were given something readable.
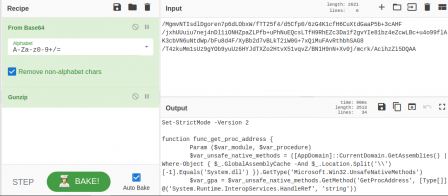
Looks like we've got powershell on our hands.
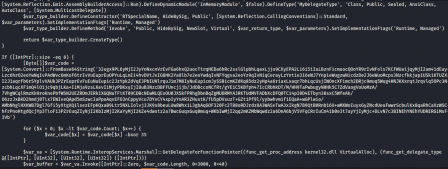
I skimmed the code and was delighted to find a delicious block of b64 data just sitting there. I once again returned to cyberchef, and decoded it.
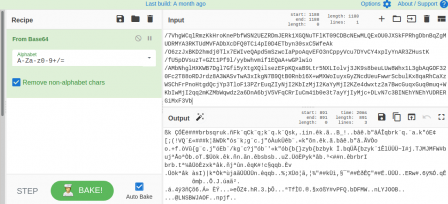
Hm. It's still unreadable. But the powershell code uses it, so perhaps there is a clue inside the script.
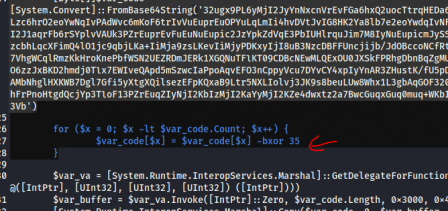
Lo and behold, the script XORs the data with an offset of 35. So let's apply that and see what we have.
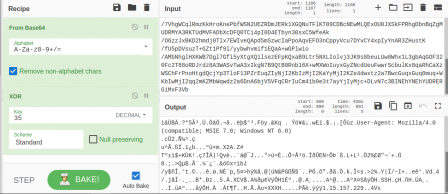
Looks like an http request with some encrypted data. Damn, probably not useful... WAIT, there's an IP address at the bottom! Success!